We often receive support requests on guide how to protect overlay and self-test applications using Enigma Protector. In this tutorial we describe how to protect such files, what are these files and why special protection features and techniques are required. If you still have any questions, please send us email at support@enigmaprotector.com.
What is overlay, self-test?
Overlay is an additional data that is added to the end of the executable file. Overlay is not being mapped to the process memory, so it is often used to store heavy data, to save the memory used by application.
Self-test is a file integrity validation method. Some applications are testing own file for modifications (whole file, or some critical part of it). Since protection modifies the file, the self-test function of such applications fail and it becomes unworkable.
Why is it so specific?
Overlay – most of problems protecting overlay files come from developers of such files and not from protection. As per our experience, most common (and not correct) way developers use the overlay is following:
- overlay is written to the file, then
- the offset to overlay is written to the file (let’s say to the end of file)
When application reads such overlay, it firstly reads it’s offset and then overlay. But after protection the file is being changed, the size and content of file also change, and the overlay offset (written to the end of file) now points to garbage data, not to overlay itself! What a problem, but how simple it could be to avoid that, if file developers could store overlay size instead of overlay offset, and just read the overlay from the offset = file size – overlay size.
Self-test – as written above, file content is being changed after protection, thus validation functions fail and file stops to work.
Where overlays are used?
We will update this list time-to-time, for now we found overlays and self-testing is used in:
- self-extracted archive, RAR, ZIP etc
- setup files, InnoSetup and others
- Adobe Captivate
- Adobe Director
- Autoplay Media Studio
How to protect?
For protection of such files we will use Virtual Box feature that allows to emulate original file in memory, so when application tries to read itself, it really reads the original virtual file, but not the protected file. And since the original file meets all necessary criteria to start (overlay position is correct, self-test functions succeed since content is original) we can still use protection features, keeping the file workable.
Go through step-by-step instructions:
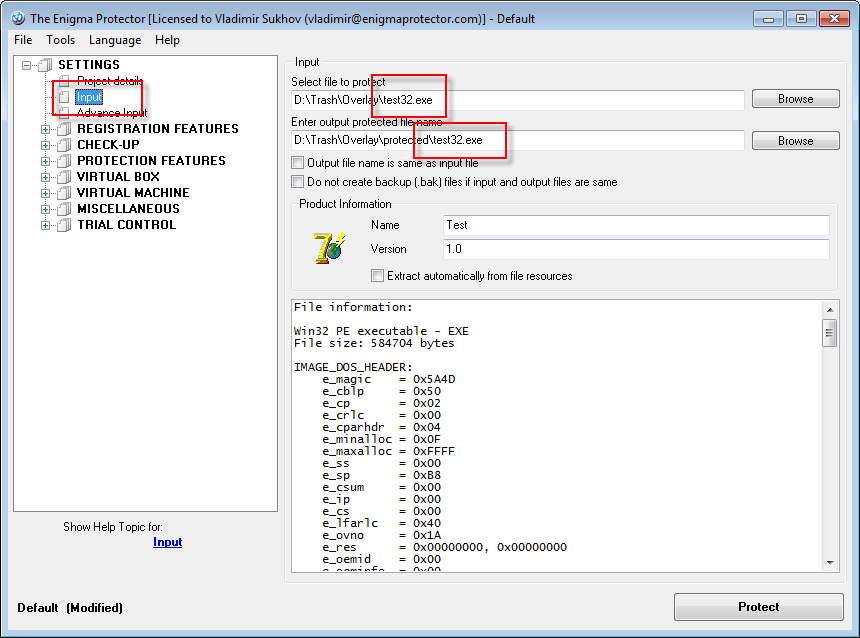
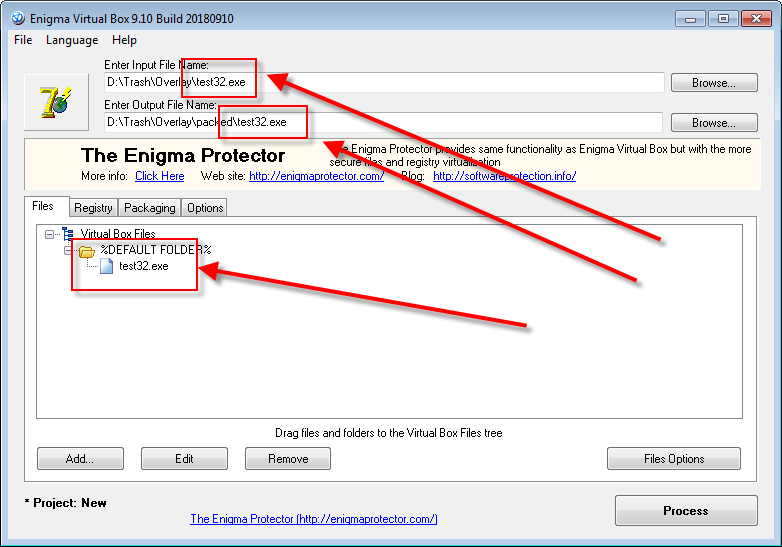
- Create a new project in Enigma Protector. Since each protection project is unique, it guaranties that all registration constants will be unique too, together with license keys (if you plan to use this feature at all)
- Select the input file on the Input panel. Set the name of the output file same as input file (just put output one in the another folder, but keep the same file name), this is very important!
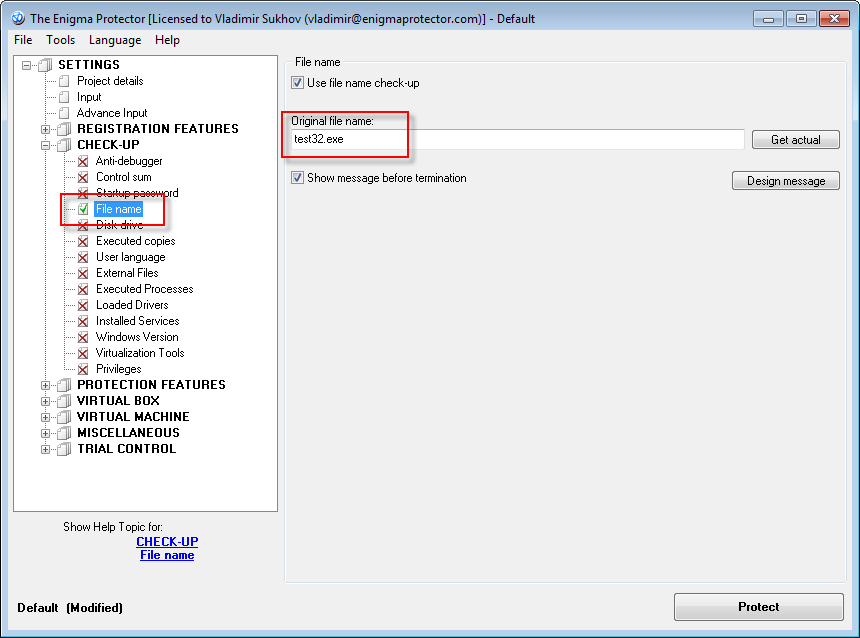
- To avoid user to change the name of protected file (that makes it damaged), use the function Checkup – File Name
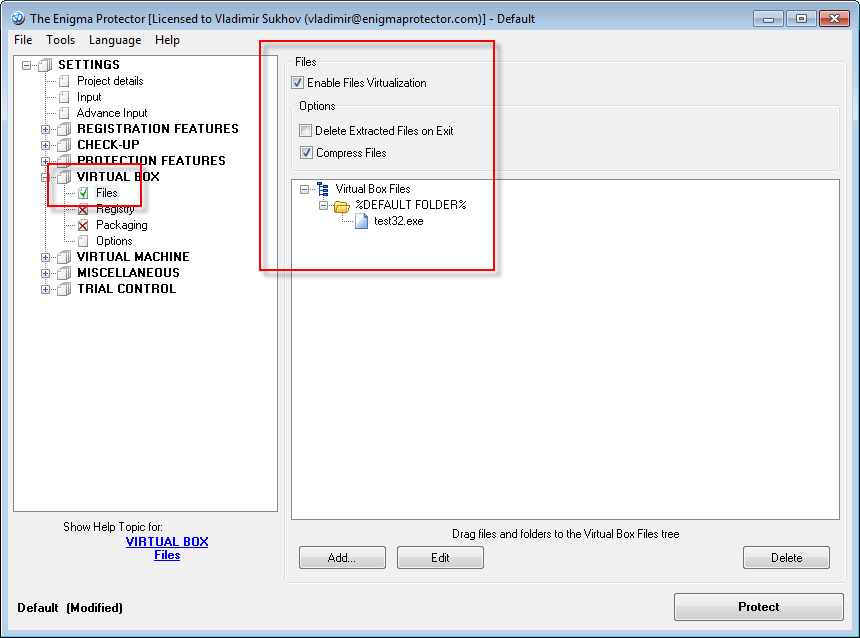
- Enable Virtual Box – Files feature and add the file you protect to %DEFAULT FOLDER% (use drag and drop from Windows Explorer or click “Add..” button to add a file). Enable file compression if required
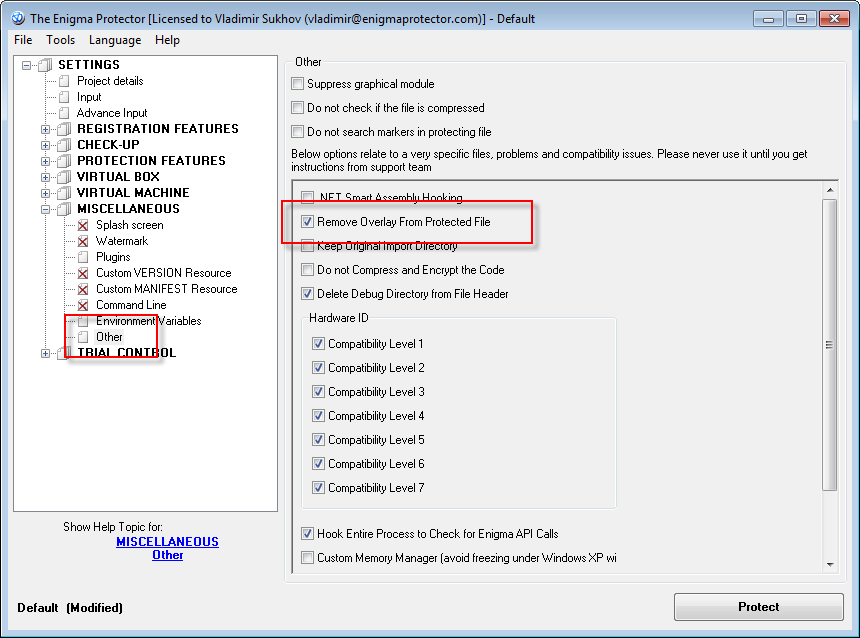
- On the Miscellaneous – Other panel, enable the option Remove Overlay From Protected File
- You can protect the file at this step to check if it works well. If it is, go ahead to enable other protection settings.
What about Enigma Virtual Box?
Enigma Virtual Box, same as Enigma Protector, also suffers from same problems.
Instructions for packing such files are same (add original file to %DEFAULT FOLDER% and keep same output file name), just there is no “Remove Overlay From Protected File” feature that is not necessary in this case.